9 Ways to Make Hybrid Work Safer & More Productive

For business leaders, employees, professionals, and management teams across most major sectors, it’s become clear that general attitudes toward work have changed remarkably in recent years.
From the rise of smart technologies, IoT devices, and advanced AI software tools to an increasingly present conversation regarding mental health and well-being in the workplace, modern hybrid work is multifaceted.
Of course, some developments have been born of necessity, with the global pandemic forcing many companies to rethink their operations in a low-contact world.
As of 2022, over 50% of US workers were found to be employed in a hybrid position, with 74% of US companies reported to be using or planning to implement a hybrid model in the future, but why has hybrid work remained so popular?
In short, providing employees with more flexibility seems to be beneficial to both staff and employers. Over 70% of employees claim that flexible schedules improve their personal well-being, and 62% feel more productive when working remotely.
And almost 60% of 597 surveyed managers appear to agree, whilst also claiming that their employees seem more concentrated and motivated when working from home.
9 Ways to Make Hybrid Work Safer & More Productive
Though the deployment of hybrid and fully remote work models are proving beneficial to a significant number of global businesses, transitioning towards such schedules isn’t always as simple as setting up a few laptops.
In fact, employers offering remote work often need to redesign existing security measures, performance management systems, and HR policies to get the most out of staff with limited in-person contact.
To help teams navigate this process, here are 9 ways to make hybrid work safer and more productive.
1. The importance of cloud-based security
Before considering any of the many intricacies of optimizing and improving hybrid work structures, it’s essential that business leaders not only develop an effective cloud-based management system but also think about how best to secure this platform from the ever-present threat of modern cybercrime. Also, they need to prioritize key management for multicloud architecture to enhance cybersecurity across diverse cloud environments.
Many organizations face challenges in securing hybrid work environments while maintaining efficiency. To tackle this, they often leverage business IT solutions that integrate cybersecurity, cloud management, and ongoing technical support.
Just as traditional in-person workplaces rely on a network of physical hardware devices to manage and maintain all essential systems, employees working in hybrid and remote roles will require an adaptive collection of software tools in order to communicate, collaborate, and perform critical tasks. This is one of the most essential digital footprint safety tips for companies that hire internationally and, therefore, have to collaborate across multiple time zones.
An effective hybrid cloud-based management system will be capable of combining the operation of all physical systems present in the main office with all virtual programs that employees are required to use during remote workdays.
This means that IT and security teams must work together to develop converged security policies designed to protect physical and virtual tools from multi-platform attacks. In the hybrid and remote work model, it’s important for organizations to adapt their cloud security measures accordingly. By adopting NIST cloud standards, businesses can design converged security policies capable of securing both physical and virtual tools across multiple platforms.
Utilizing trusted cloud penetration testing tools can further support these efforts by identifying vulnerabilities across diverse cloud environments. In addition, implementing robust endpoint and vulnerability management solutions helps organizations continuously monitor, detect, and remediate weaknesses across employee devices and connected systems before they can be exploited. This is essential in maintaining strong defense mechanisms against cyber threats while supporting a flexible working environment. For teams maturing their cloud defenses, understanding the differences between XDR and EDR can clarify tooling choices for threat detection, response orchestration, and cross-surface visibility in hybrid environments.
There are many ways to achieve this. For example, providing employees with a secure VPN to be used when requesting remote-access to any work-related programs will prevent famous hackers from viewing each user’s IP address, in turn averting sophisticated criminals from stealing identifiable or valuable company data. For organizations with budget constraints, cheap proxies can offer an affordable way to add an extra layer of IP protection and anonymity for remote workers, making enterprise-grade security more accessible to small and medium-sized businesses. The best kind of IPs for remote workers are generally ISP proxies as those appear human-like and don’t get flagged.
Additionally, teams should implement some form of data encryption to obscure all communications sent between company systems.
This is done by discovering which VPN protocol you should choose that suits your specific requirements and considerations. Factors such as network security, performance, compatibility with your devices and operating systems, ease of setup and use, and the level of privacy you need all play a role in the decision-making process.
Data published in IBM’s Cost of a Data Breach Report 2019 found that over 50% of severe data breaches were caused by malicious or criminal attacks stemming from unprotected company data, information that would become unusable if properly encrypted at source.
Business insurance can be essential in mitigating the financial consequences of data breaches caused by malicious attacks, as highlighted in IBM’s Cost of a Data Breach Report 2019.
2. Provide comprehensive cybersecurity training
Designing and implementing considered security policies may be crucial to the successful operation of a hybrid workplace, though these protocols will only be effective if employees are well-trained in how best to utilize and follow them. As part of this training, it’s important to familiarize staff with the DORA security regulations, which provide a comprehensive framework for managing and mitigating digital risks in a hybrid environment.
Research published in Verizon’s 2022 Data Breach Investigations Report found that 82% of cyber-attacks involve an element of human error, meaning employers must invest in personalized and frequent cybersecurity training programs to make hybrid work much safer.
With less time spent in the office under the watchful eye of trained security professionals, employees must be confident in their ability to spot and avoid common online risks.
Risks like social engineering threats such as ransomware and phishing attacks that studies suggest may be involved in as many as 98% of breaches. To protect staff, begin by creating actionable guidance.
Effective cybersecurity policies can include:
- Requesting ID verification before accessing secure company systems
- Instructing staff to never use personal USB sticks or external devices
- Report lost or stolen credentials within a predetermined time frame
- Ensure that staff never click on emails from unrecognized sources
- Forward suspicious emails to a dedicated security response address
- Prevent staff from accessing personal accounts using company hardware
Teaching staff about specific cybersecurity risks like online gaming risks and other personal uses of company devices that can lead to cyberattacks
Smart password policies
In addition to behavioral cybersecurity training, security teams must implement breach and attack simulation as well as advanced password management protocols to further prevent the possibility of severe cyberattacks
One recent study found that 54% of employees admit to using the same password to secure multiple different accounts, with supporting data finding workers may be wasting up to 30% of their time resetting lost passwords.
To prevent this significant loss of productivity and to ensure that sensitive credentials are far less likely to become compromised, security staff must implement strong password protections.
Primarily, staff must be advised to avoid using common phrases and sequential numbers in their passwords, as many of these credentials can be compromised in under a second using modern hacking techniques.
Security experts instead recommend that employees choose to utilize passwords between 12-16 characters long that also contain a combination of capital letters and numbers as well as unique symbols.
Finally, security teams should integrate multi-factor authentication (MFA) alongside all devices used to access company data, as this methodology can prevent up to 99% of common cyber-attacks.
Moreover, integrating a robust static residential proxies solution can add an extra layer of security by masking or hiding IP addresses and protecting against potential cyber threats.
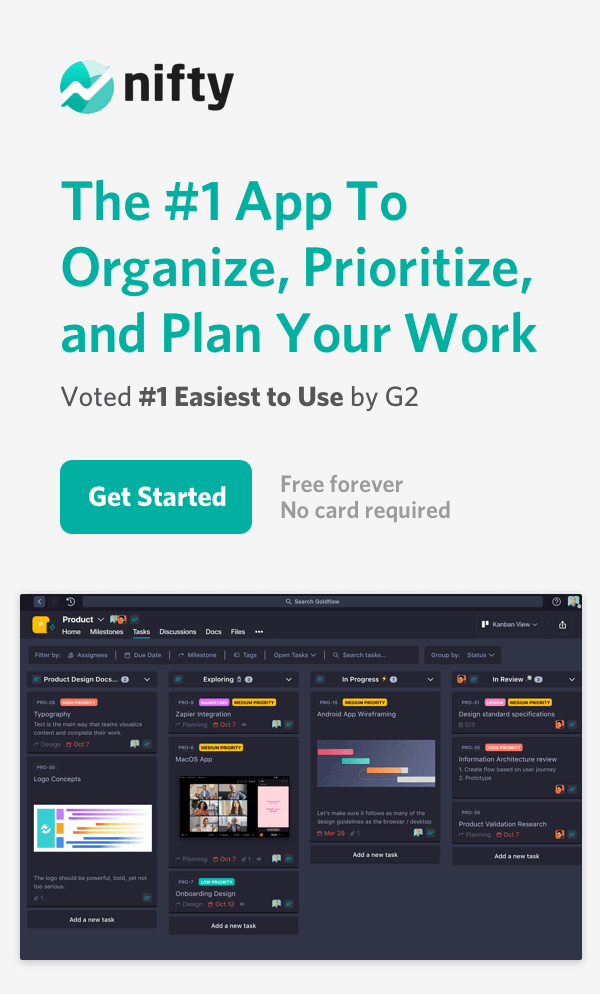
3. Choose the right project management tool:
Choosing the right project management tool is crucial, especially in today’s hybrid work environment, where teams are often spread across various locations and time zones.
Nifty offers a range of features that not only facilitate effective collaboration but also streamline project timelines and enhance time tracking, making it an ideal choice for teams in hybrid work environments.
Collaboration
Collaboration lies at the heart of successful project management, and Nifty excels in this aspect. Its intuitive interface allows team members to communicate seamlessly, share files, and assign tasks, regardless of their physical location.
With real-time updates and notifications, everyone stays in the loop, ensuring smooth coordination and minimizing miscommunication. The tool’s centralized workspace ensures that team members can access all relevant project information, reducing the need for constant back-and-forth communication.
Timelines
In a hybrid work environment, maintaining project timelines becomes more challenging due to different schedules and availability.
Nifty addresses this concern by offering robust timeline management features. Team members can create and visualize project timelines, set milestones, and allocate resources accordingly.
This allows for better planning and resource allocation, ensuring projects stay on track even with remote team members. Additionally, Nifty’s automated reminders and deadline notifications help keep everyone accountable, further enhancing productivity and adherence to timelines.
Time tracking
Accurate time tracking is another critical aspect of project management, especially in a hybrid work environment where flexible schedules are common. Nifty simplifies time tracking by providing integrated timers and time logs.
Team members can log their work hours easily, providing transparency and accountability. This feature enables project managers to accurately track project progress, identify bottlenecks, and allocate resources effectively.
Moreover, it allows for fair and accurate invoicing, making it beneficial for both freelancers and agencies working on client projects.
4. Restrict access to personal devices
One of the major benefits of operating within a hybrid work model is the flexibility that staff is given to approach their duties in a way that suits their own unique working style. However, with a less rigid structure of management overseeing daily workflows, workers may pick up some undesirable habits.
The most concerning of these potential issues from a security standpoint would be the blurred line of use between professional and personal devices when accessing sensitive company data.
Security staff may have worked hard to ensure that all password protections, VPNs, and digital access control policies are able to prevent data breaches, only for a personal device to expose new vulnerabilities.
If an employee is to log into a company-owned platform from a personal device, admins will be unable to verify that the hardware has been appropriately maintained or updated to prevent novel malware, ransomware, or virus programs from posing a significant risk to connected company-owned systems.
This risk also extends to employees accessing personal social media and e-commerce accounts from company-owned computers.
Not only can these pursuits contribute to a significant loss of productivity, with data indicating some remote staff waste as much as 14% of a standard working week engaged in personal activities, but browsing unapproved sites could expose new avenues for criminals to target.
Worryingly, recent reports state that 32% of hybrid and remote workers are known to use apps and software programs that haven’t been approved by IT or security departments, with 92% found to be using personal tablets or smartphones to complete work tasks.
With this in mind, it’s advised that employers only permit monitored access to work systems using company-owned hardware devices.
5. Implement a principle of least privilege
For businesses transitioning towards hybrid and remote work models, it can be tempting to simply provide all employees with access to shared devices in an effort to limit time and resource waste by designing a bespoke access policy.
However, failing to segment user access to essential programs will only increase the available attack surface exposed to sophisticated attacks and threats.
By implementing a principle of least privilege used to govern all access control policies, employers can ensure that staff will only ever have access to the specific data required for teams to reasonably perform their day-to-day responsibilities.
In other words, the role of the employee will always be used to determine which systems, files, hardware, and specific data resources they’re able to interact with.
One way to achieve this is through the use of multi-factor authentication, whereby security staff can lock system access behind an additional ID verification system.
Using the technology already present in modern smartphones, configurations can be developed that require staff to use biometrics such as facial recognition or fingerprint scans to access work systems, with biometrics being hard to fabricate.
Additionally, security teams may choose to utilize a role-based access control (RBAC) model. This will involve the creation of a software program capable of analyzing staff credentials to grant user access based entirely on the employee’s position in the company.
To further reduce vulnerabilities, integrating the best DNS security software can help block malicious domains and prevent unauthorized access attempts at the network level. You can further enhance your DNS security with the EasyDMARC DNS Record Checker, which verifies your DNS configurations, helps detect spoofing risks, and strengthens overall email and network protection.
For example, all issued password and ID card data can be stored in a company database and internally assigned to a specific role. Login functions can then be programmed to only permit access to users flagged with matching credentials.
In practice, an RBAC model would automatically segment access to sensitive information to reduce the likelihood of security breaches. Low-risk programs like chat services and bulletin boards can be made accessible to anybody, though only those flagged as managers could access sensitive data.
In addition to limiting access and safeguarding data based on user roles, understanding the importance of SCIM provisioning for streamlined identity management becomes vital in a hybrid work environment. Implementing a system that automatically manages user identities across various applications ensures only the right individuals have access to sensitive information, further bolstering security.
6. Physical security in hybrid environments
Of course, creating a safer and more productive hybrid working environment will require more than the strengthening of company cybersecurity measures, with installed physical security systems also in need of a considered redesign.
With less structured office hours being observed by flexible staff or workers engaged in coworking schemes, and this freedom also being extended to security and IT teams, adaptive systems must be created. When implementing new security protocols, seamless IT onboarding for remote employees is also crucial to ensure efficient access to necessary resources.
Employers should start with the development of a cloud-based security management system capable of combining both the monitoring and operation of all physical security hardware from a single remote-access platform, as doing so will enable security teams to provide 24/7 support in a flexible schedule.
To achieve this, employers should consult with a professional business security camera installation or physical security integration team to design a bespoke system suited to their unique requirements.
By choosing to install IoT products and IP-enabled security cameras, alarms, sensors, and access control devices, security staff will be provided a holistic view of all systems through carefully considered integrations.
For example, security cameras can be connected to IoT motion sensors and access readers installed throughout the main office, with automated functions designed to alert security staff in real time if an intruder attempts to access the property without valid credentials.
Security staff will be notified of such events via a message sent to their smartphones, allowing teams to provide remote security support.
7. Optimize physical security systems
Simply connecting all physical security devices together within a cloud-based management platform will allow security and IT teams to monitor and adjust all active systems from a remote position, but to provide comprehensive support in a hybrid environment, additional optimizations should be pursued.
For instance, considering that 85% of Americans own a smartphone, modern offices can be optimized to make use of mobile-access systems that allow flexible workers to safely enter and exit the property at any time of day.
Personalized credentials can be sent directly to users’ smartphones, which in turn can be used to interact with touchless access control readers to provide 24/7 monitored access for employees.
As mobile credentials consist only of digital data, employers can avoid the security risks associated with lost or stolen key cards and fobs, with admins able to remotely monitor all access events in real-time, immediately revoke potentially compromised credentials, and utilize advanced MFA protections.
A further benefit to the use of cloud-based security systems and IoT smart technology devices is the ability to configure automated building management functions and create a secure business cloud storage, with these developments well suited to hybrid workplaces as on-site security and IT staff will not be required to work in the office at all times.
Possible smart technology automation includes:
- Rule-based access control (RuBAC) – Access control door locks can be programmed to only grant property access at certain times of day, this means that flexible workers can be permitted safe access to suit their schedules without the need for on-site security guards
- AI-informed surveillance cameras – AI data analytics software, like license plate and facial recognition camera, can be integrated alongside installed security cameras to automatically alert security teams in real time to the presence of suspicious vehicles or potential intruders
- Automated lockdown functions – Door locking mechanisms can be connected to access control readers and on-site IoT alarms with the system programmed to automatically seal all access points if devices are tampered with or if suspicious activity is detected in the property
- Asset tracking systems – Valuable office equipment like laptops and electronic devices can be monitored via installed software and assigned barcodes to assist security and IT teams in keeping track of company-owned property loaned out to employees working flexible hours
8. Utilize performance management software
Recent studies show that 85% of modern employees are not engaged whilst at work, with supporting data indicating a clear correlation between employee engagement and overall productivity.
One factor known to improve employee engagement is to provide workers with frequent personalized feedback, something 43% of highly engaged employees receive, but this can be difficult in hybrid environments.
To ensure that staff feels supported, valued, and satisfied when working in hybrid and flexible roles, HR teams should utilize smart technology in the form of monitored performance management software.
These systems are designed to use intelligent data analytics to assess the quality of each employee’s work to highlight specific skill sets and processes that individuals may benefit from developing further.
When integrated alongside existing work programs, modern performance management software can be configured to send automated responses as part of a wider employee recognition system, as well as offer additional support through data analysis to help staff identify personal development targets.
Research shows that supporting staff in this way can help to reduce employee turnover by almost 15%, with 92% of employees agreeing that detailed feedback is essential for improving performance in a working environment, illustrating the benefits of implementing performance management tools.
9. Promote collaboration with smart technology
Collaboration between employees and key departments within most modern businesses is essential for facilitating a productive and positive workplace environment, with 75% of employers claiming that teamwork and collaboration are important in a productive workplace and 97% of executives believing poor alignment between teams and department heads have a detrimental impact on any project’s outcome.
Promoting collaboration between in-person teams is often a fairly straightforward task, with team leaders able to simply schedule regular meetings or informal drop-in sessions to keep track of ongoing projects, though, in a hybrid setting, it can be difficult to plan around unconventional employee schedules.
Thankfully, employers can make use of smart technology systems to ensure that both remote and in-office workers are able to combine their expertise and skill sets at all times.
For example, software programs like Slack or Microsoft Teams can be used to connect employees in a virtual environment to view, adjust and edit documents remotely, though hardware collaboration tools may also be utilized.
Microsoft Teams data can be backed up with third-party software, such as NAKIVO backup for Microsoft 365, to maintain employee collaboration security.
There is also modern video conferencing software with which employees can have automatic recordings of their calls and access them whenever in need of previously discussed information or in case they have been absent.
Smart whiteboards can be installed in meeting rooms to provide a visual tool for in-person and remote workers to interact with, allowing both teams to adjust documents in real-time during vital idea-forming sessions.
Additionally, video conferencing systems can be integrated alongside these devices to further bridge the gap between traditional in-office and modern remote communications to improve productivity.
Summary
As modern businesses and employees continue to adapt in line with changing attitudes towards work, leaders must develop new policies, procedures, and physical systems designed to not only solve novel issues but also provide staff with a safer and more productive environment conducive to hybrid work.
By taking the time to assess the unique requirements of each workplace and implementing converged security systems capable of protecting staff from physical and cybersecurity threats, employers can help employees to thrive in flexible work structures.
Cloud-based systems can be used to provide 24/7 support, mobile access control can allow staff to manage their own property access, and intelligent performance management systems can help to improve employee engagement and productivity metrics.
Provided that business owners consult with their employees to develop a unique combination of hardware and software systems suited to their needs, most studies suggest that hybrid and flexible work models are beneficial to modern companies, helping to create a safer and more productive professional environment.